In today’s digital age, protecting sensitive information is more critical than ever. With cyber threats on the rise and the growing complexity of IT systems, organizations must adopt comprehensive data security strategies to ensure that their information remains secure, particularly throughout the lifecycle of their IT assets. This includes everything from procurement to disposal, particularly the IT Asset Disposition (ITAD) process, where proper data destruction is a key aspect. But, while data destruction is undeniably important, it’s not the whole story.
In this article, we’ll explore into the ITAD lifecycle, analyze why data destruction alone is insufficient to ensure complete cybersecurity, and examine best practices that organizations can adapt to mitigate risks and safeguard their data.
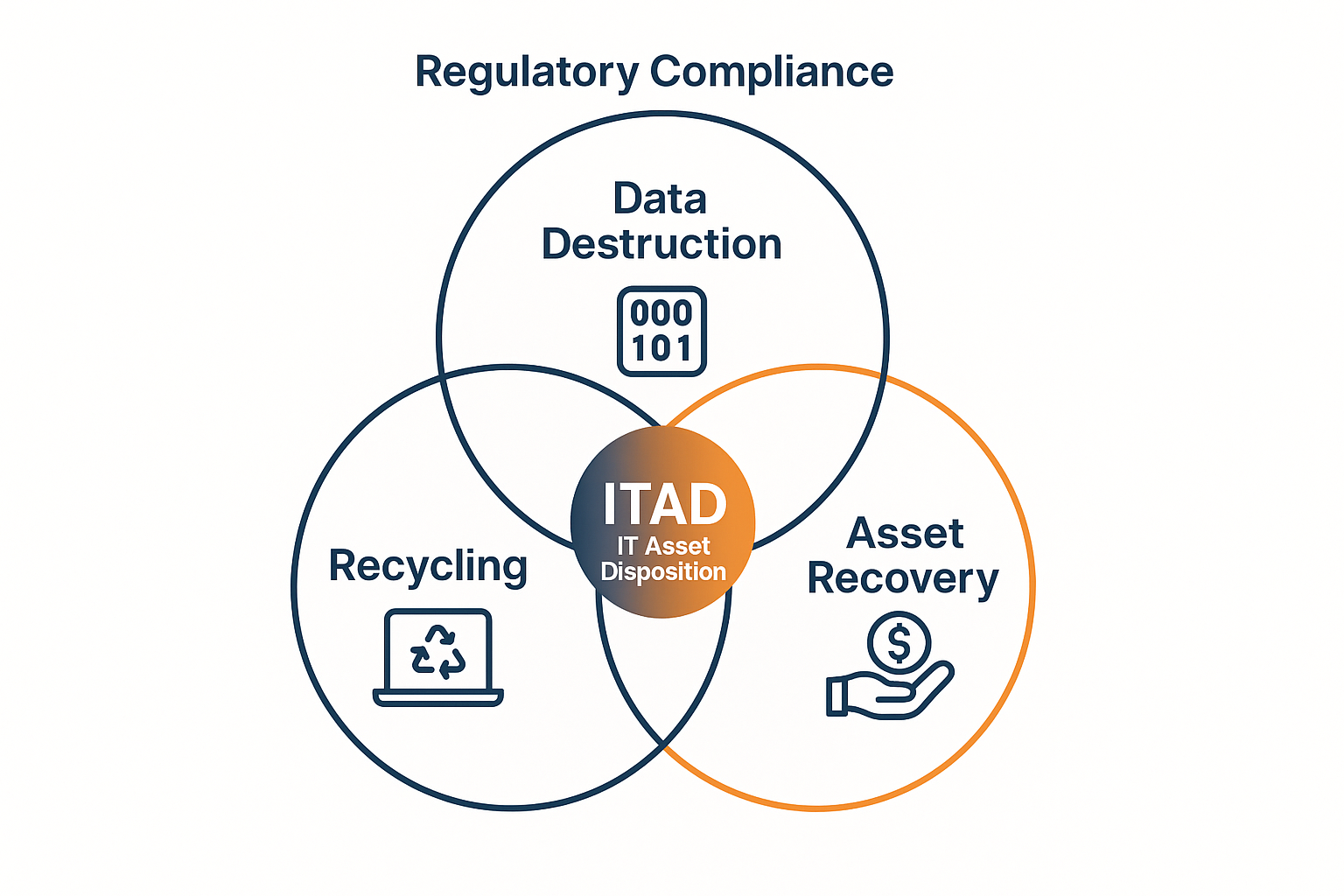
What Is ITAD (IT Asset Disposition)?
IT Asset Disposition (ITAD) refers to the process of securely retiring and disposing of outdated, surplus, or end-of-life IT equipment securely. This could include computers, smartphones, hard drives, servers, printers, and other electronic devices.
In the modern ITAD process, data destruction is one of the most critical tasks. However, to truly protect your organization’s information and prevent breaches, this process must be part of a comprehensive cybersecurity strategy.
Why Data Destruction Alone Isn’t Enough
While data destruction, such as wiping, degaussing, or physically destroying hard drives, is a significant part of the ITAD process, it’s not a standard strategy. Let’s break down why this isn’t enough:
1. Data Recovery Threats Post-Destruction
Even after a hard drive has been wiped or destroyed, there’s still a risk of data recovery. Advanced data recovery tools can sometimes retrieve partial or complete data from damaged or overwritten drives, especially when destruction isn’t thorough. Simple data wiping often leaves remnants that cybercriminals can exploit.
2. Improper Disposal of Hardware
Data destruction focuses on eliminating data, but may overlook the proper disposal of physical assets. Improper disposal can lead to environmental and security risks. Simply discarding or reselling old hardware without ensuring it has been adequately destroyed or decommissioned can expose your organization to unnecessary threats.
3. Data Security Breaches in Secondary Markets
If IT assets are sold or repurposed without proper data destruction, they can end up in the hands of unauthorized individuals or third-party organizations. These entities might find ways to retrieve and misuse the information stored on these devices. The secondary market for used electronics is vast, and inadequate ITAD practices could lead to serious cybersecurity breaches.
4. Inadequate Tracking and Reporting
Another critical component that data destruction fails to address is ensuring proper tracking and auditing of disposed assets. Without robust tracking, it’s challenging to guarantee that all assets have been properly wiped and disposed of. This lack of transparency increases the risk of lost or misplaced data and exposes organizations to compliance failures.
5. Compliance and Legal Requirements
Organizations are often required to comply with strict data protection regulations, such as GDPR, HIPAA, or PCI-DSS. Data destruction is just one element of compliance. Without a comprehensive, auditable, and secure ITAD process, an organization may inadvertently violate these regulations, resulting in costly fines and reputational damage.
Key Aspects of a Comprehensive ITAD and Data Security Strategy
To fully protect your organization’s data throughout the ITAD lifecycle, a well-rounded cybersecurity strategy is essential. Here are the critical components:
1. Comprehensive Data Destruction
Data destruction should go beyond simple data wiping. It’s important to use industry-standard techniques, such as:
- Data wiping (using certified software to overwrite data multiple times).
- Degaussing (using a magnetic field to erase data from hard drives).
- Physical destruction (crushing, shredding, or melting the storage devices).
- Certified disposal partners (working with vendors who follow secure, compliant procedures).
2. Detailed Asset Tracking and Reporting
Maintain an accurate inventory of all devices, with clear records of their decommissioning and destruction. This allows you to verify that each piece of hardware has been securely handled and destroyed. Your organization should also ensure that every step in the ITAD process is thoroughly documented and reported, accompanied by certificates of destruction for added accountability.
3. Environmental Responsibility
Proper disposal isn’t just about security—it’s about environmental responsibility. Ensure that your ITAD provider follows eco-friendly disposal practices, including recycling materials and disposing of hazardous substances in accordance with environmental standards.
4. Third-Party Vendor Vetting
If you’re outsourcing ITAD services, work with certified vendors that comply with industry standards (such as NAID or R2 certification). These certifications ensure that vendors use best practices when handling sensitive data.
5. Employee Training and Awareness
Employees involved in the ITAD process are trained on proper data destruction techniques, compliance requirements, and security policies. This helps reduce human error, which could lead to data breaches.
Best Practices for ITAD Security
To help you navigate the complexities of the ITAD process and maintain robust data security, here are some best practices:
Best Practice
Description
Use Certified ITAD Vendors
Select vendors that follow certified destruction and disposal processes, ensuring data is irretrievably destroyed. |
Implement End-to-End Security
Data destruction should be part of an overall security strategy that includes encryption and tracking. |
Create Clear Policies and Procedures
Ensure your organization has clear, well-communicated policies on ITAD that include data protection protocols. |
Ensure Compliance with Legal Standards
Stay up to date with legal and regulatory standards for data protection (GDPR, HIPAA, etc.). |
Track Assets from Start to Finish
Maintain a thorough audit trail for all hardware assets, from their acquisition to final disposal. |
Regularly Review Your ITAD Process
Periodically audit your ITAD practices to ensure they align with evolving security standards and threats. |
Conclusion
While data destruction is undeniably a cornerstone of IT asset disposition, it’s only one piece of the puzzle. To truly secure your data and protect your organization from cyber threats, a holistic approach to the ITAD lifecycle is essential. This involves integrating comprehensive data destruction methods with proper tracking, compliance, environmental responsibility, and effective management of third-party vendors.
By implementing a robust ITAD strategy, your organization can ensure that it remains protected against data breaches and security threats, now and in the future. Cybersecurity is a shared responsibility that spans beyond the destruction of data—it’s about ensuring that every touchpoint in the IT lifecycle is secure.
So, don’t settle for just data destruction—elevate your ITAD process to meet the cybersecurity demands of today and tomorrow with MNC services.






Companies often neglect to have written standards and policies around their cybersecurity. Why? Because dozens of them are usually needed, covering everything from equipment management to backup procedures, admin credentialing, remote work policies, and so much more. But it’s well worth the effort.