In today’s rapidly evolving digital landscape, ensuring the security of sensitive data during IT asset disposition (ITAD) is more critical than ever. With the increasing number of cyber threats, businesses must adhere to stringent cybersecurity standards and regulations to protect sensitive information. Among the most important of these are the NIST (National Institute of Standards and Technology), HIPAA (Health Insurance Portability and Accountability Act), and ISO (International Organization for Standardization) standards. But what do these standards mean for ITAD, and how can organizations meet these requirements while ensuring data security? Let’s delve deeper to gain a better understanding.
What is IT Asset Disposition (ITAD)?
IT asset disposition refers to the process of securely disposing of or recycling obsolete IT equipment, including computers, hard drives, and other hardware. This is an essential process for businesses, as outdated devices often contain sensitive data that could pose a security risk if not correctly handled. The goal of ITAD is to ensure that these devices are either safely destroyed or recycled in compliance with data security standards.
Why Meeting NIST, HIPAA, and ISO Standards is Crucial for ITAD?
For businesses, especially those in regulated industries, ensuring the safe destruction of data during ITAD is not just about maintaining trust with customers—it’s a legal and regulatory requirement. Meeting industry standards, such as NIST, HIPAA, and ISO, helps organisations mitigate the risk of data breaches, avoid substantial fines, and protect their reputation.
Let’s explore these standards in more detail and how they relate to ITAD.
1. NIST (National Institute of Standards and Technology)
NIST provides guidelines and frameworks for increasing cybersecurity and managing risks associated with IT systems. Specifically, NIST Special Publication 800-88 outlines best practices for media sanitization, ensuring that all sensitive information is fully erased from hardware before it’s disposed of.
NIST Cybersecurity Best Practices for ITAD:
- Media Sanitization: NIST recommends three primary methods for sanitizing data: clear, purge, and destroy. These methods ensure that data is irretrievably wiped from devices.
- Documenting the Process: NIST advises keeping a record of the sanitization process, including serial numbers and proof of destruction, to demonstrate compliance.
- Certified Equipment: Using certified ITAD vendors who meet NIST standards ensures that a thorough process is followed.
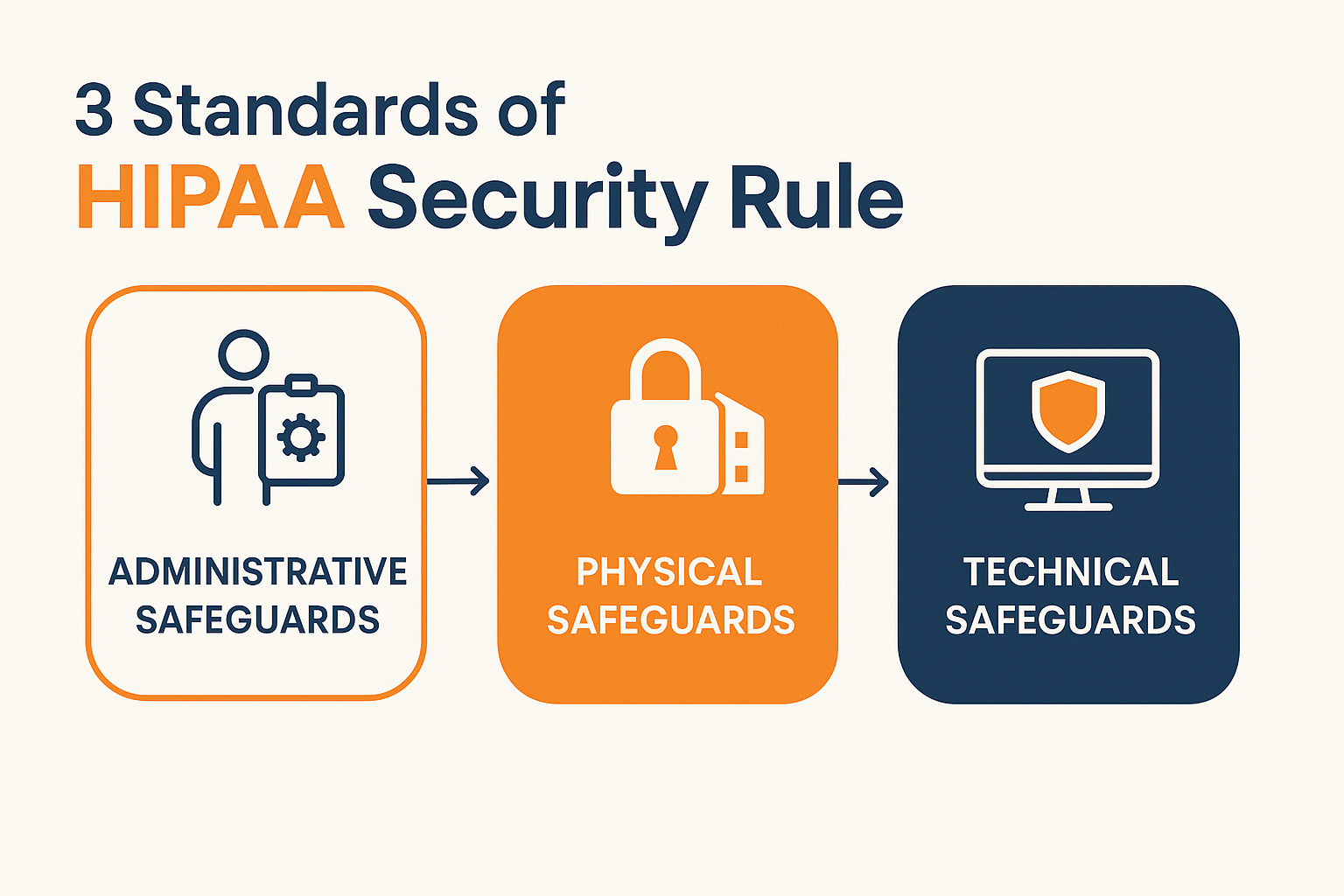
2. HIPAA (Health Insurance Portability and Accountability Act)
For healthcare organizations, HIPAA mandates strict guidelines for protecting patient health information (PHI). When disposing of IT assets that may contain PHI, organizations must ensure that the data is destroyed in a manner that prevents unauthorized access.
HIPAA Compliance Best Practices for ITAD:
- Data Destruction: HIPAA requires the destruction of PHI stored on old devices. This includes using certified methods of sanitization to ensure data cannot be reconstructed or retrieved.
- Vendor Management: HIPAA also holds healthcare organizations responsible for ensuring their ITAD vendors comply with security protocols. Ensure that the ITAD vendor follows HIPAA-compliant data destruction procedures.
- Documentation: Keep thorough documentation of the data destruction process, including certificates of destruction, to provide an audit trail.
3. ISO (International Organization for Standardization)
ISO standards are globally recognized and provide guidelines on various aspects of business processes, including information security. ISO 27001, for example, focuses on establishing, implementing, and maintaining an Information Security Management System (ISMS), while ISO 27002 outlines best practices for managing sensitive data.
ISO Best Practices for ITAD:
- Secure Disposal: ISO emphasizes the importance of securely disposing of information in a manner that prevents unauthorized access to sensitive data. Following ISO 27001 can help businesses define their security requirements for ITAD (Information Technology Asset Disposal).
- Third-Party Audits: Organizations should ensure that ITAD vendors are ISO certified, demonstrating that they follow best practices for secure data destruction.
- Access Control: Only authorized personnel should have access to sensitive data during the disposal process. ISO standards recommend using encryption and other access controls during this phase.
Practical Cybersecurity Best Practices for ITAD
Now that we’ve covered the key standards, here are some practical tips for businesses looking to adhere to these cybersecurity standards during IT asset disposal:
Best Practice
Description
Select a Certified ITAD Vendor |
Choose an ITAD vendor who adheres to NIST, HIPAA, and ISO standards and provides certification of destruction. |
Implement Secure Data Wiping |
Use data sanitization methods, such as NIST’s clear, purge, and destroy procedures, to ensure that all data is unrecoverable. |
Encrypt Devices Before Disposal |
Encrypt data on devices before they are disposed of to add an extra layer of security in case sanitization fails. |
Document the Entire Process |
Keep thorough records of the disposal process, including certificates of destruction and vendor details. |
Schedule Regular Audits |
Conduct audits to verify compliance with industry standards and ensure that your ITAD processes are secure and compliant. |
Conclusion
Meeting NIST, HIPAA, and ISO standards during IT asset disposition is crucial for ensuring that sensitive data is protected and regulatory requirements are met. Whether you’re in healthcare, finance, or any other industry, understanding the importance of proper ITAD processes will help safeguard your business from data breaches and other security risks. By adhering to best practices, such as selecting certified vendors, securely erasing data, and maintaining accurate documentation, organizations can navigate the complexities of ITAD while keeping sensitive data secure.
If you’re looking to implement a secure and compliant IT asset disposition process, don’t hesitate to consult with experts who specialize in this field to ensure the highest level of protection for your data.







Some leaders consider business and technology objectives interchangeable, allowing one to inform the other. Those that align their information technology systems with their overall business strategy have the best chances of achieving their short- and long-term objectives.